Damages and Damage Allocation
Based on Dr. Cole’s industry experience at various large organizations, including Lockheed Martin and McAfee, he is able to defend his allocation strategies in court with his real-world experience. He has real world experience evaluating, buying, and selling patents and software components. To complete these transactions, he has had to use internal models and processes for evaluating value on these technologies and patents. Unlike more mature product lines like pharmaceuticals, in cybersecurity, there aren’t many previous models to follow. Very few if any published models in journals, reports, or previous cases to follow exist for cybersecurity. Dr. Cole not only works on damages for cybersecurity cases but also for networking and information security.
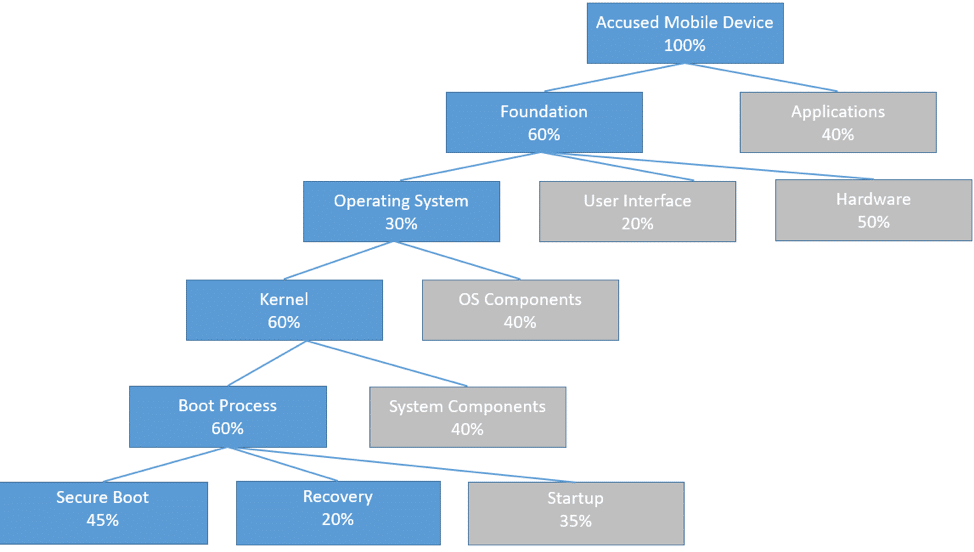
Case Study 1 – A high profile client had acquired several patents, one of which was for a system of verifying, validating, and securing mobile devices upon startup. One of the most popular mobile device manufacturers in the world had devices that followed this same startup process, which ultimately infringed on the client’s patent. When Dr. Cole was brought onto the case, there was an economist already working on the damages, but he was struggling on the allocation portion of the damages, which would ultimately be derived from the technological experience Dr. Cole has. Dr. Cole broke down the entire accused device into a decision tree. Using the decision tree, he was then able to calculate the allocation of the infringing technology for the entire product overall. Using this information, the economist was then able to take that allocation and calculate the financial values to present in the case.
